Log In
Sign Up
Wipro Interview Guide
Wipro Hiring Process (For Freshers – Wipro Elite NTH)
Wipro recruits fresh graduates from across India for the role of Project Engineer through its placement program called Elite NTH.
Total Interview Stages: 4
- Online Assessment
- Quantitative Aptitude
- Logical Reasoning
- Verbal Ability
- Essay Writing
- Coding
- Interview Round
- Technical + HR (combined)
Job Role Offered
Wipro hires through:
- On-Campus Recruitment
- Off-Campus Recruitment
For freshers, Wipro mainly offers one profile:
Project Engineer — ₹3.5 LPA (may vary based on company performance each year)
Salary & Benefits
Employees hired as Project Engineers get a structured salary package with multiple benefits such as allowances, insurance, and performance-based perks.
Detailed Wipro Recruitment Rounds
1. Online Assessment (Major Elimination Stage)
- About 75% of candidates get filtered out at this step.
- The assessment consists of 48 questions to be solved in 48 minutes
- All sections are qualifying in nature, which means you must clear each of them.
2. Essay / Written Communication Round
- You need to write a 200–300 word essay on a given topic
- Time provided: 20 minutes
- This stage evaluates grammar, clarity, flow, and written English
3. Interview Round (Technical + HR combined)
- This is a single round where both technical and HR questions are asked.
- Duration: around 60–90 minutes
- About 92% of candidates are rejected here, so preparation is essential.
Topics expected in the Technical Interview
- Data Structures & Algorithms
- DBMS & SQL
- OOPs concepts
- Core CS subjects
- Your academic projects & certifications
- Coding knowledge
Topics expected in the HR Interview
- Self-introduction, strengths & weaknesses
- Questions based on resume & hobbies
- Situational & behavioral questions
- Common HR questions like:
- Why should we hire you?
- Where do you see yourself in 5 years?
- Are you ready to relocate?
- Sometimes puzzles and psychometric questions are also included
About the Company – Wipro
- Founded: 29 December 1945
- Founder: M.H. Hasham Premji
- Headquarters: Bangalore, India
- Wipro offers services in:
- IT consulting
- Cloud and Cybersecurity
- Digital transformation
- Robotics & Artificial Intelligence
- Data Analytics and more
50 Wipro Technical interview questions
1. What is OOPS?
OOP stands for Object-Oriented Programming.
It uses objects and classes to structure code logically.
Main principles are abstraction, inheritance, polymorphism, and encapsulation.
2. What is a Class and Object?
A class is a blueprint that defines properties and behaviors.
An object is an instance created from a class.
Multiple objects can be created from a single class.
3. Explain Inheritance.
Inheritance allows one class to acquire properties of another class.
It helps in code reusability.
Example: Dog inherits features from Animal.
4. What is Polymorphism?
Polymorphism means performing a task in multiple ways.
It can be compile-time (method overloading) or runtime (method overriding).
It improves code flexibility.
5. What is Encapsulation?
Encapsulation hides internal data and exposes only required information.
It is done using getters and setters.
This improves security and reduces data misuse.
6. Difference between Overloading and Overriding.
Overloading occurs within the same class with different parameters.
Overriding happens in parent-child classes with the same method signature.
Overloading is compile-time; overriding is runtime.
7. What is a Constructor?
A constructor initializes objects while creating them.
Its name is same as class name.
It has no return type.
8. What is an Abstract Class?
An abstract class contains abstract and non-abstract methods.
It cannot be instantiated directly.
It provides a partial blueprint for child classes.
9. What is an Interface?
An interface contains only abstract methods (before Java 8).
It defines a contract that implementing classes must follow.
Multiple inheritance is possible using interfaces.
10. What is DBMS?
DBMS is software used to store, manage, and retrieve data.
It enables efficient handling of large datasets.
Examples: MySQL, Oracle, PostgreSQL.
11. What is SQL?
SQL stands for Structured Query Language.
It is used to manage and manipulate relational databases.
Commands include DDL, DML, DCL, and TCL.
12. Difference between Primary Key and Unique Key.
Primary Key uniquely identifies each record and cannot be NULL.
Unique Key also prevents duplicate values but allows one NULL.
A table can have one Primary Key but many Unique Keys.
13. What is Normalization?
Normalization removes redundancy from database tables.
It organizes data into multiple related tables.
It improves efficiency and consistency of data.
14. What is a Join?
Join combines rows from multiple tables based on related columns.
Types include INNER, LEFT, RIGHT and FULL JOIN.
It helps fetch meaningful relational data.
15. What is an Array?
An array is a collection of similar data elements stored in continuous memory.
It has a fixed size.
Elements are accessed using index numbers.
16. What is a Linked List?
Linked List is a dynamic data structure consisting of nodes.
Each node contains data and a reference to the next node.
It supports dynamic memory allocation.
17. Difference between Array and Linked List.
Array has fixed size; Linked List is dynamic.
Array allows random access; Linked List allows sequential access.
Insertion and deletion are faster in Linked List.
18. What is a Stack?
Stack follows LIFO (Last In First Out) order.
Push and pop are the major operations.
Useful for expression evaluation and backtracking.
19. What is a Queue?
Queue follows FIFO (First In First Out) order.
Insertions occur at the rear, deletions at the front.
Used in OS scheduling and resource management.
20. What is Recursion?
Recursion is a function calling itself repeatedly.
It must have a base condition to stop.
Common in tree and graph traversal.
21. What is Time Complexity?
Time complexity measures how fast an algorithm runs as input grows.
It uses Big-O notation like O(n), O(log n), etc.
It helps compare algorithm performance.
22. What is Binary Tree?
A binary tree is a data structure where each node has at most two children.
Nodes are arranged as left and right children.
Useful for search, routing, and hierarchical data.
23. What is Operating System?
OS is software that manages hardware and resources.
It provides interface between user and computer.
Examples: Windows, Linux, macOS.
24. What is Process and Thread?
Process is an executing program with its own memory.
Thread is a lightweight unit of execution inside a process.
Multiple threads can run inside one process.
25. What is Deadlock?
Deadlock is a situation where two processes wait for each other indefinitely.
It occurs due to resource locking.
OS uses techniques to detect or prevent it.
26. What is a CPU Scheduler?
CPU scheduler allocates CPU time to processes.
It decides the execution order of tasks.
Examples include FCFS, Round Robin, and SJF.
27. What is Cloud Computing?
Cloud computing provides computing resources over the internet.
It includes storage, servers, and databases on demand.
Models include IaaS, PaaS, SaaS.
28. What is Big Data?
Big Data refers to extremely large datasets beyond traditional processing limits.
It is defined by 5 V’s: Volume, Velocity, Variety, Veracity, and Value.
Technologies include Hadoop and Spark.
29. What is Machine Learning?
ML enables computers to learn from data and improve accuracy.
It removes need for explicit programming for predictions.
Algorithms include regression, clustering, and neural networks.
30. What is an API?
API stands for Application Programming Interface.
It allows two applications to communicate with each other.
Widely used in web and mobile development.
31. What is TCP/IP?
TCP/IP is a networking model for communication over the internet.
TCP handles data transmission reliability; IP handles addressing.
It enables global data transfer.
32. What is HTTP and HTTPS?
HTTP is a protocol for web communication without encryption.
HTTPS includes SSL/TLS encryption for secure data transfer.
HTTPS is used for safe transactions.
33. What is DNS?
DNS converts domain names into IP addresses.
It acts like an internet phonebook.
Without DNS, users would need to remember numeric IPs.
34. What is Git?
Git is a version control system for tracking code changes.
It supports collaboration among developers.
Common commands are git init, git add, git commit, git push.
35. What is Agile Model?
Agile is a software development methodology based on iterative releases.
Customer feedback is taken regularly.
It speeds up development with flexibility.
36. What is SDLC?
SDLC stands for Software Development Life Cycle.
It defines phases like planning, development, testing, and deployment.
It ensures structured software development.
37. What is a Framework?
A framework is a pre-built environment for faster development.
It provides reusable libraries and structure.
Examples include Spring, Django, and React.
38. What is Exception Handling?
Exception handling manages runtime errors without crashing the program.
Statements like try, catch, and finally are used.
It improves reliability of applications.
39. What is Multithreading?
Multithreading allows multiple threads to run concurrently.
It increases program performance and responsiveness.
Used in gaming, animation, and servers.
40. What is Virtual Memory?
Virtual memory extends physical RAM using disk storage.
It helps handle large programs smoothly.
Paging is a common technique.
41. What is a Pointer (C/C++)?
A pointer stores the memory address of a variable.
It enables dynamic memory and efficient data access.
Operators used are * and &.
42. What is Dynamic Memory Allocation?
It allocates memory at runtime instead of compile time.
Functions like malloc, calloc, and free are used in C.
It prevents memory wastage.
43. What is JSON?
JSON stands for JavaScript Object Notation.
It is a lightweight format for data exchange.
Used widely in APIs and web applications.
44. What is REST API?
REST API uses HTTP methods to interact with applications.
Common methods are GET, POST, PUT, DELETE.
It is stateless and scalable.
45. What is String Immutable in Java?
String objects cannot be modified once created.
Any modification creates a new String object.
This improves security and memory optimization.
46. What is Static Keyword?
Static keyword allocates memory once per class.
Static members are shared across all objects.
Useful for constants and utility methods.
47. What is Final Keyword?
Final prevents modification of variable, method, or class.
Final variable becomes constant; final class cannot be inherited.
Improves data safety.
48. What is Garbage Collection?
Garbage collection automatically removes unused memory in Java.
It prevents memory leaks.
It runs in the background without manual control.
49. What is a Wrapper Class?
Wrapper classes convert primitive data types into objects.
Examples: Integer, Boolean, Character.
Used in Collections and generics.
50. What is Compiler vs Interpreter?
Compiler converts whole code to machine language at once.
Interpreter translates code line by line.
Compiler is faster during execution; interpreter is slower but flexible.
Wipro Coding Questions
Question 1:
Consider a sorted array arr[] of size N. The objective is to design an algorithm to eliminate duplicate elements from the array. Implement a function that efficiently modifies the input array in-place, resulting in a new array without any duplicate elements. Clearly outline the steps of your algorithm and provide any necessary explanations
Example:
Input: arr[] = {2, 2, 2, 2, 2}
Output: arr[] = {2}
Explanation: All the elements are 2, So only keep one instance of 2.
Input: arr[] = {1, 2, 2, 3, 4, 4, 4, 5, 5}
Output: arr[] = {1, 2, 3, 4, 5}
Question 2:
A number can always be represented as a sum of squares of other numbers. Note that 1 is a square and we can always break a number as (1*1 + 1*1 + 1*1 + …). Given a number n, find the minimum number of squares that sum to X.
Example:
Input: n = 100
Output: 1
Explanation:
100 can be written as 102. Note that 100 can also be written as 52 + 52 + 52 + 52, but this representation requires 4 squares.
Input: n = 6
Output: 3
Question 3:
Given an integer N. The task is to find the first N Fibonacci numbers.
Example:
Input: n = 3
Output: 0 1 1
Input: n = 7
Output: 0 1 1 2 3 5 8
Question 4:
Given a matrix of dimensions N x M, the task is to compute the transpose of the matrix. The transpose of a matrix is achieved by interchanging its rows with columns and columns with rows. Formally, for a matrix A of size N x M, the transpose A^T is obtained by transforming each element A[i][j] to A[j][i].
Develop an algorithm to calculate the transpose of the given matrix efficiently, and provide a detailed explanation of the steps involved.
Example:
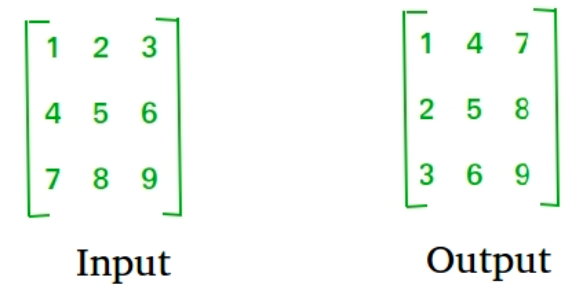
Question 5:
Consider two integers, fact and n. The objective is to determine the largest power of n that divides the factorial of fact (denoted as fact!).
Mathematically, the problem can be defined as finding the exponent of n in the prime factorization of fact!. The prime factorization of a factorial involves determining the highest power of each prime number that divides the factorial.
Design an algorithm to efficiently compute the largest power of n that divides fact! and provide a detailed explanation of the steps involved. Include any relevant pseudocode or code snippets as needed. Additionally, analyze the time and space complexity of your solution.
Example:
Input :
fact = 5, n = 2
Output :
3
Explanation:
Value of 5! is 120. The largest power
of 2 that divides 120 is 8 (or 23
Input :
fact = 146, n = 15
Output :
35
Question 6:
Problem Statement:
Given a Linked List, implement the following operations to insert a new node:
Insertion at the Front:
Insert a new node at the beginning of the linked list.
Insertion After a Given Node:
Insert a new node after a specified node in the linked list.
Insertion at the End:
Insert a new node at the end of the linked list.
Clearly outline the algorithms for each insertion operation, providing step-by-step details and any necessary pseudocode. Additionally, discuss the time complexity of each operation and any relevant considerations.
Question 7:
Given an unsorted array of positive integers, find the number of triangles that can be formed with three different array elements as three sides of triangles. For a triangle to be possible from 3 values, the sum of any of the two values (or sides) must be greater than the third value (or third side).
Example:
Input: arr= {4, 6, 3, 7}
Output: 3
Explanation: There are three triangles
possible {3, 4, 6}, {4, 6, 7} and {3, 6, 7}.
Note that {3, 4, 7} is not a possible triangle.
Input: arr= {10, 21, 22, 100, 101, 200, 300}.
Output: 6
Explanation: There can be 6 possible triangles:
{10, 21, 22}, {21, 100, 101}, {22, 100, 101},
{10, 100, 101}, {100, 101, 200} and {101, 200, 300}
Question 8:
Given a string, the objective is to reverse the order of the words within the string.
Example:
Input: “Hello World”
Output: “World Hello”
Design an algorithm to efficiently reverse the order of words in the given string. Clearly outline the steps of your algorithm and provide any necessary pseudocode or code snippets. Additionally, analyze the time and space complexity of your solution.
Question 9:
Consider an expression string exp. The task is to develop a program that examines the correctness of pairs and the order of the following symbols within the given expression: “{“, “}”, “(“, “)”, “[“, “]”.
Design an algorithm to determine whether the symbols in the expression are correctly paired and ordered. Provide a detailed explanation of the steps involved, including any relevant pseudocode or code snippets. Additionally, discuss the time and space complexity of your solution.
Example:
Input: exp = “[()]{}{[()()]()}”
Output: Balanced
Explanation: all the brackets are well-formed
Input: exp = “[(])”
Output: Not Balanced
Explanation: 1 and 4 brackets are not balanced because
there is a closing ‘]’ before the closing ‘(‘
Question 10:
Consider an array of integers arr[] with a size of N. The objective is to design a program to rotate the elements of the array to the left by a specified number of positions, denoted by the integer ‘d’.
Formally, the task is to implement an algorithm that shifts the array elements to the left by ‘d’ positions, ensuring that the relative order of elements is maintained.
Example:
Input:
arr[] = {1, 2, 3, 4, 5, 6, 7}, d = 2
Output: 3 4 5 6 7 1 2
Input: arr[] = {3, 4, 5, 6, 7, 1, 2}, d=2
Output: 5 6 7 1 2 3 4
Question 11:
Write an efficient program to count the number of 1s in the binary representation of an integer.
Example:
Input : n = 6
Output : 2
Binary representation of 6 is 110 and has 2 set bits
Input : n = 13
Output : 3
Binary representation of 13 is 1101 and has 3 set bits
Question 12:
Given an array A[] of n numbers and another number x, the task is to check whether or not there exist two elements in A[] whose sum is exactly x.
Example:
Input: arr[] = {0, -1, 2, -3, 1}, x= -2
Output: Yes
Explanation: If we calculate the sum of the output,1 + (-3) = -2
Input: arr[] = {1, -2, 1, 0, 5}, x = 0
Output: No
Question 13:
Given an array of size n, arrange the first k elements of the array in ascending order and the remaining n-k elements in descending order.
Example:
Input: arr[] = {5, 4, 6, 2, 1, 3, 8, 9, -1}, k = 4
Output: 2 4 5 6 9 8 3 1 -1
Input: arr[] = {5, 4, 6}, k = 2
Output: 4 5 6
Question 14:
Given a range [n,m], find the number of elements that have an odd number of factors in the given range (n and m inclusive).
Example:
Input : n = 5, m = 100
Output : 8
The numbers with odd factors are 9, 16, 25,
36, 49, 64, 81 and 100
Input : n = 8, m = 65
Output : 6
Input : n = 10, m = 23500
Output : 150
Question 15:
Given a range [n,m], find the number of elements that have an odd number of factors in the given range (n and m inclusive).
Example:
Input : n = 5, m = 100
Output : 8
The numbers with odd factors are 9, 16, 25,
36, 49, 64, 81 and 100
Input : n = 8, m = 65
Output : 6
Input : n = 10, m = 23500
Output : 150
Question 16:
Given two given numbers a and b where 1<=a<=b, find the number of perfect squares between a and b (a and b inclusive).
Example:
Input : a = 3, b = 8
Output : 1
The only perfect square in the given range is 4.
Input : a = 9, b = 25
Output : 3
The three perfect squares in given range are 9,
16 and 25
Question 17:
Given an array of integers, sort the first half of the array in ascending order and the second half in descending order.
Example:
Input : arr[] = {10, 20, 30, 40}
Output : arr[] = {10, 20, 40, 30}
Input : arr[] = {5, 4, 6, 2, 1, 3, 8, 9, 7 }
Output : arr[] = {2, 4, 5, 6, 9, 8, 7, 3, 1 }
Question 18:
In an examination scenario, you are presented with K sorted arrays, each of size N. Your assignment is to develop an algorithm for merging these arrays into a single sorted output. Formulate a solution that efficiently merges the K sorted arrays and produces the final sorted result. Provide the code for your algorithm along with the necessary explanation, demonstrating your ability to handle and manipulate sorted arrays in a merging context.
Example:
Input: K = 3, N = 4, arr = { {1, 3, 5, 7}, {2, 4, 6, 8}, {0, 9, 10, 11}}
Output: 0 1 2 3 4 5 6 7 8 9 10 11
Explanation: The output array is a sorted array that contains all the elements of the input matrix.
Question 19:
Determine the methodology to identify a peak element within a given 2D Array or Matrix. Develop an algorithm that can effectively pinpoint a peak element in the matrix, adhering to the specified task requirements.
Example:
Input: [[10 20 15], [21 30 14], [7 16 32]]
Output: 1, 1
Input: [[10 7], [11 17]]
Output : 1, 1
Question 20:
Within a collection of strings, your task is to employ Binary Search to identify the longest common prefix. Devise a solution that efficiently determines the shared prefix among the given strings, utilizing the principles of Binary Search.
Example:
Input: strings = [“flower”, “flow”, “flight”]
Output: Longest Common Prefix: ‘fl’
Question 21:
Given the Binary code of a number as a decimal number, we need to convert this into its equivalent Gray Code. Assume that the binary number is in the range of integers. For the larger value, we can take a binary number as a string.
Example:
Input: 1001
Output: 1101
Explanation: 1001 -> 1101 -> 1101 -> 1101
Input: 11
Output: 10
Explanation: 11 -> 10
Question 22:
Given a number N and its reverse R. The task is to find the number obtained when the number is raised to the power of its own reverse. The answer can be very large, returning the result modulo 109+7.
Example:
Input : N = 2, R = 2
Output: 4
Explanation: Number 2 raised to the power of its reverse 2 gives 4 which gives 4 as a result after performing modulo 109+7
Input : N = 57, R = 75
Output: 262042770
Explanation: 5775 modulo 109+7 gives us the result as 262042770
Question 23:
Given a string of lowercase characters from ‘a’ – ‘z’. We need to write a program to print the characters of this string in sorted order.
Example:
Input : bbccdefbbaa
Output : aabbbbccdef
Question 24:
You have been given a series (1*1) + (2*2) + (3*3) + (4*4) + (5*5) + … + (n*n), find out the sum of the series till nth term.
Example:
Input : n = 3
Output : 14
Explanation : (1*1) + (2*2) + (3*3)
Input : n = 5
Output : 55
Explanation : (1*1) + (2*2) + (3*3) + (4*4) + (5*5)
Question 25:
Find the lowest common ancestor of two nodes in a binary tree.
Question 26:
Find the maximum flow in a flow network using Ford-Fulkerson or Edmonds-Karp algorithm.
Question 27:
We are given two sorted arrays. We need to merge these two arrays such that the initial numbers (after complete sorting) are in the first array and the remaining numbers are in the second array
Example:
Input: ar1[] = {10}, ar2[] = {2, 3}
Output: ar1[] = {2}, ar2[] = {3, 10}
Input: ar1[] = {1, 5, 9, 10, 15, 20}, ar2[] = {2, 3, 8, 13}
Output: ar1[] = {1, 2, 3, 5, 8, 9}, ar2[] = {10, 13, 15, 20}
Question 28:
There are N houses built in a line, each of which contains some value in it. A thief is going to steal the maximum value of these houses, but he can’t steal in two adjacent houses because the owner of the stolen houses will tell his two neighbors left and right sides. The task is to find what is the maximum stolen value.
Example:
Input: hval[] = {6, 7, 1, 3, 8, 2, 4}
Output: 19
Explanation: The thief will steal 6, 1, 8 and 4 from the house.
Input: hval[] = {5, 3, 4, 11, 2}
Output: 16
Explanation: Thief will steal 5 and 11
Question 29:
How to determine if a binary tree is height-balanced?
Question 30:
Given two strings. The task is to check whether the given strings are anagrams of each other or not. An anagram of a string is another string that contains the same characters, only the order of characters can be different. For example, “abcd” and “dabc” are an anagram of each other.
Examples:
Input: str1 = “listen” str2 = “silent”
Output: “Anagram”
Explanation: All characters of “listen” and “silent” are the same.
Input: str1 = “gram” str2 = “arm”
Output: “Not Anagram”


